
Executive Summary
In today's digital landscape, cryptography has become an essential aspect of IT security, particularly as regulations and data privacy needs surge. However, many organizations struggle to manage their cryptographic protocols and to fully understand their risk posture due to a lack of modernization and automation. While the rest of the digital world was moving toward DevOps and continuous delivery, cryptography remained a blind spot, with most organizations relying on outdated processes that cannot keep up with the complexity of modern IT.
The consequences of this outdated approach to cryptography are numerous and costly for any organization. Unmanaged cryptographic artifacts can cause critical application outages, while demonstrating cryptographic compliance relies on outdated processes that do not meet management or auditor expectations. Enforcing internal cryptographic policies is difficult, leading to data encryption or key management policies being ignored. When it comes to switching from one cryptographic standard to another, the entire organization may be left without an established solution to handle the migration efficiently. Case in point: it took some organizations up to 10 years to migrate from SHA-1.
Adding to the challenges of outdated cryptography is the looming threat of quantum computers. Sensitive data is vulnerable to "store now, decrypt later" cyber attacks that will only increase as quantum computing advances. It is imperative that organizations modernize their cryptography protocols and incorporate automation to ensure they are protected from current and future threats.
The U.S. National Institute of Standards and Technology (NIST) recently selected four quantum-resistant algorithms for standardization. To protect your organization, it is essential to gain a comprehensive understanding of its risk posture and to plan the migration process to new protocols immediately.
This is an opportunity to take control of your cryptography by implementing cryptographic agility throughout your organization’s IT infrastructure. This guide will help you understand the anticipated cybersecurity implications of quantum computers and provides a migration process to prepare your organization for both present and future cryptographic demands.
The Urgent Need for Cryptographic Migration
In recent years, the proliferation of cyber attacks has been staggering, fueled by organized crime and nation-state sponsored hacking. In the context of this threat level, the emergence of quantum computing is accelerating the need to move away from current encryption standards to post-quantum cryptography (PQC). A powerful, fault-tolerant quantum computer is expected to enable hackers to quickly decipher the cryptographic algorithms your organization currently relies on to secure its data. This puts RSA, elliptic curve cryptography (ECC), and Diffie-Hellman key exchange, among others, at risk of being compromised once the first capable quantum computers become available.
The process of transitioning to new cryptographic standards will take many years depending on the size and complexity of your organization. As a result, industry experts and government officials encourage starting the process now to protect sensitive data. Regulators in several western countries have released requirements or recommendations urging organizations to commence the migration process immediately.
At SandboxAQ, we are committed to educating information security teams on these emerging risks and to providing mitigation and migration strategies to improve your cybersecurity posture.
The Importance of Cryptographic Agility
Cryptographic agility refers to the capability of a security system to encapsulate new cryptographic primitives or algorithms, allowing for seamless replacement of outdated or compromised components. Cryptographic agility is an essential element of an enterprise security posture because it allows organizations to quickly adapt to new challenges and to stay ahead of the curve in the ever-changing security landscape.
An agile cryptographic security system must maintain an inventory of cryptographic components and update them as necessary to stay current with the latest standards and best practices. This adaptability enables the system to swiftly and effectively respond to new threats. The goal is to empower developers to make changes without the need to master unfamiliar cryptography or data security while also retaining autonomy over their code.
In a DevOps environment, this involves incorporating cryptographic algorithms and protocols into the continuous integration and continuous delivery (CI/CD) pipeline. This includes the ability to automatically test and evaluate the strength and suitability of cryptographic algorithms as well as to easily switch to more secure or appropriate algorithms.
Cryptographic agility ensures the system can effectively respond to evolving compliance requirements and threats without requiring significant changes to the underlying infrastructure, which is essential to maintain uninterrupted business and mission continuity.
[SIDEBAR]
Cryptographic Agility: The ability to encapsulate cryptographic primitives or algorithms, making it easy to switch and replace these primitives as new standards emerge. An agile cryptographic security system should create a cryptographic inventory and, if needed, adapt it to evolving compliance requirements and threats, without requiring significant infrastructure changes, ensuring business continuity.
Transitioning to PQC is inevitable, and preparing now is necessary for the migration process to be efficient and effective. In 2022, the U.S. White House and Office of Management and Budget issued memorandums that require federal agencies to comply with NIST-approved quantum-resistant encryption algorithms and protocols, and the U.S. National Security Agency set a 2035 deadline for adoption of PQC across national security systems. Also in 2022, the U.S. Congress passed the Quantum Computing Cybersecurity Preparedness Act, cementing into law the need for federal government IT systems to transition to PQC.
Although past cryptographic migrations have been challenging, adopting cryptographic agility will help your organization remain one step ahead of ever-changing requirements by creating an infrastructure that is built to quickly evolve.
NIST-Standardized PQC Algorithms
NIST has been working for the past six years on a standardization process to select algorithms that are resistant to both classical and quantum cyber attacks. The first four NIST-standardized PQC algorithms were announced in July 2022.
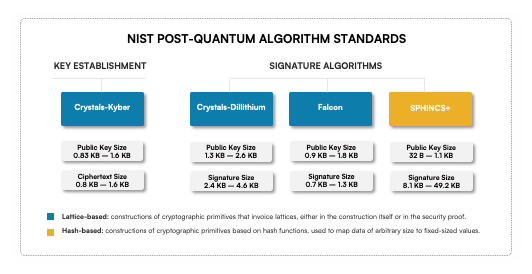
The NIST standardization process included both key encapsulation mechanisms (KEM) and digital signature algorithms (DSA), arguably two of the most important cryptographic building blocks for secure communication. NIST selected various algorithms that have different performance profiles based on public key sizes, cipher text/signature sizes, computation time, ease of secure implementation, and security assumptions.
[SIDEBAR]
The PQC Algorithms Selected by NIST
CRYSTALS-KYBER: This key establishment algorithm has small encryption keys, making it easy for two parties to exchange keys quickly. It also has a fast speed of operation, which is essential for applications that require real-time communication.
CRYSTALS-Dilithium: This signature algorithm has a high efficiency and has been recommended by NIST as the primary PQC algorithm. It provides a high level of security and is suitable for various applications.
FALCON: This high-efficiency algorithm is suitable for applications that require small signatures. It is an excellent alternative to CRYSTALS-Dilithium in cases where the signature size is a concern.
SPHINCS+: Although this hash-based algorithm is larger and slower compared to the others, it will be standardized as a back-up option. Because it uses a different mathematical approach, it will provide an additional layer of security in addition to lattice-based algorithms.
As a complement to these standardization activities, NIST’s National Cybersecurity Center of Excellence (NCCoE) launched the Migration to Post-Quantum Cryptography project in July 2022. NCCoE selected SandboxAQ as one of a select group of industry partners for the project that were invited to help develop best practices to ease the migration from current public-key cryptography algorithms to replacement algorithms that are resistant to quantum computer-based attacks.
Applying a Robust Security Suite
At SandboxAQ, we understand that complying with new government guidelines and protecting your organization’s data can be complex and time-consuming. That's why we offer a robust, crypto-agile software platform that helps you manage cryptography more efficiently and makes the transition to quantum-resistant cryptography as smooth as possible. The SandboxAQ Security Suite will not only help your organization remain compliant with ever-changing requirements, but will also enable it to seamlessly upgrade encryption and remain secure against threats, both current and future.
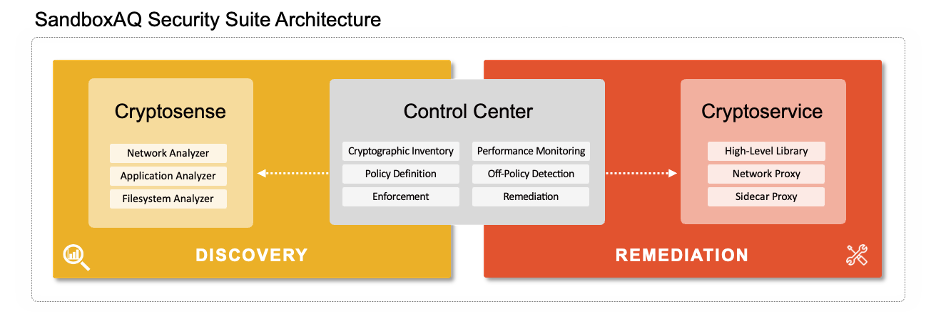
Our Security Suite includes three modules:
- Cryptosense retrieves information from three types of analyzers that run on hosts and network devices: the Network Analyzer, the Application Analyzer, and the Filesystem Analyzer.
- The Control Center provides a comprehensive, dashboard view of your cryptographic inventory, including artifacts, libraries, algorithms, and protocols. The Control Center also includes benchmarking tools to monitor your cryptography's performance and policy management.
- Cryptoservice enables remediation and automated enforcement to respond to off-policy violations, while continuously optimizing cryptography across your entire organization.
SandboxAQ's Security Suite provides a wide range of benefits for enterprise organizations, including:
- Continuous inventory management: Our suite enables you to create and manage a continuous inventory of all cryptographic assets across your IT infrastructure. This inventory provides full visibility into the artifacts, libraries, algorithms, protocols, and their applications, allowing you to identify and manage potential security risks in real-time.
- Control and policy management: SandboxAQ software helps you to deploy a control and policy management system that ensures future cryptographic compliance. Define your policies, both standardized (such as FIPS 140 or PCI DSS) and custom, and be notified of any off-policy cryptography usage. Our platform also enables you to perform remediation and automated enforcement to respond to off-policy violations in your system.
- Point-to-point cryptographic enforcement: Our suite allows you to add point-to-point cryptographic enforcement tools for critical areas of your IT infrastructure. This enables you to achieve a high level of security in critical areas, ensuring sensitive data remains protected.
- Seamless transition to cryptographic agility: Our platform allows you to implement PQC, minimizing time and costs. We provide optimized cryptography across your entire organization in a continuous manner, enabling you to seamlessly transition to new requirements.
- Cryptographic sovereignty: With SandboxAQ, you will gain sovereignty over your cryptography, minimizing the need for external resources. We will train your personnel to ensure your organization can perform all critical phases and activities, allowing you to maintain control over your security measures.
Overall, SandboxAQ will help you to stay ahead of the curve and protect your organization's sensitive data from both current and future cyber threats. Our Security Suite provides full visibility and monitoring of your cryptographic posture, cryptographic policy management, and deployment and enforcement of quantum-resistant cryptography protocols. With SandboxAQ you can achieve a high level of security, comply with government and industry standards, and prepare for the future of cybersecurity.
Request a SandboxAQ Security Suite demo today and take the first step toward a more secure future.
Related Articles
Join The GBI Impact Community
Sign up to make an impact and hear about our upcoming events
By registering anywhere on the site, you agree with our terms and privacy policy



