The 4 Essential Pillars of a Scalable TPCRM Program
Toyota’s factories, which pump out over 10 million vehicles every year, screeched to a halt in February 2022. The culprit? A cyber attack on one of their third-party vendors—a plastic supplier named Kojima. To prevent hackers from levying serious damage, the automotive giant had to suspend 28 production lines at 14 different plants, losing an untold amount of money.

Regardless of how tight an organization’s internal cybersecurity measures are, like Toyota, nearly anyone can fall victim to an attack via one of their vendors. This highlights the need for a scalable third-party cyber risk management (TPCRM) program that systematically addresses the risk posed by the vendors you use to keep your business running.
We partnered with cyber risk experts to dive into what it takes to build a scalable TPCRM program, breaking it down into four pillars. The panel for our webinar consisted of Gideon Rasmussen, CISSP at Virtual CSO, Shay Colson, Managing Partner, Cyber Diligence at Coastal Cyber Risk Advisors, Gary Phipps, VP, Risk Solutions at CyberGRX, and moderator Peter Finter, CMO at CyberGRX. Listen in to the discussion now:
https://youtu.be/6EMrrPIPqlM
Pillar 1: Strategy
On average, the typical enterprise uses around 5,800 third-party tools. Each of these presents a unique entry point for hackers. As a result, organizations need a strong strategy to limit the risk of attacks. Often, however, a TPCRM program is born out of a reactive, instead of proactive, approach.
An audience poll reveals security practitioners are using a variety of tools to manage TPCRM, with spreadsheets topping the list.
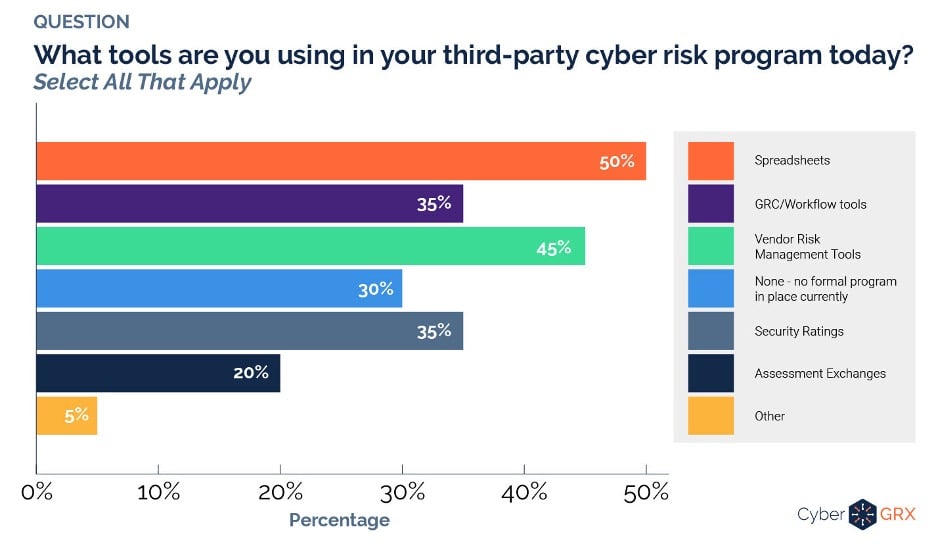
Our panelists expressed concern over the 30% with no formal TPCRM program in place currently, especially given the rise in cyber threats.
As Shay Colson explains, the inflection points that spurn a TPCRM program typically falls into one of three buckets:
- An organization sees the effects of a breach on another company and decides to take action.
- An enterprise experiences a close call and decides to take steps to prevent a more serious incident.
- Regulatory pressures force a company to tighten their defenses against third-party breaches.
Regardless of what inspires an organization to take action, according to Gideon Rasmussen, the focus of your strategy should be business continuity. “I’m always focused on operations risks, including privacy fraud and insider threats,” Mr. Rasmussen begins. “ So when looking at third party risk from an operational risk perspective, there are vendors companies have to work with, but at the same time, they have to be evaluated.”
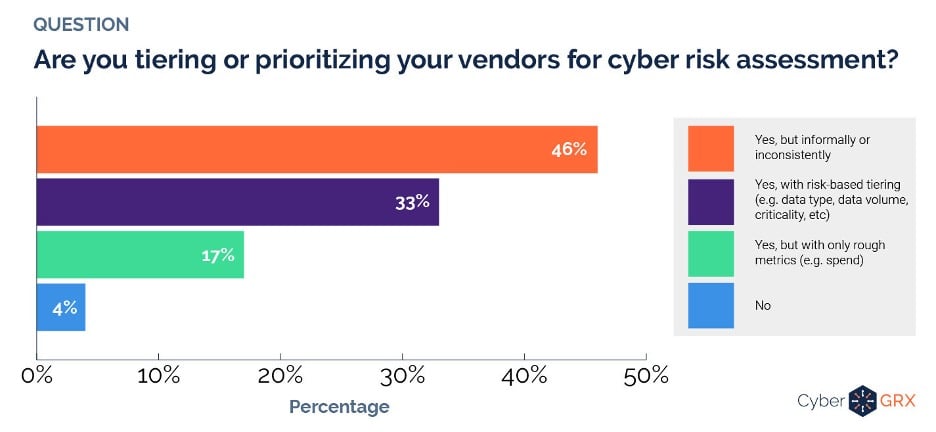
However, according to a poll taken during the webinar, the ways in which companies go about doing this vary considerably. 46% informally or inconsistently tier or prioritize vendors as they assess the cyber risks they pose, 17% do so with only rough metrics, 33% tier in a systematic way, and 4% don’t tier vendors according to risk at all.
Pillar 2: Process
The process of implementing a TPCRM program has to center around getting the right stakeholders on board. This is a challenge for many companies, with 38% of respondents reporting that executive team support is their biggest TPCRM implementation challenge.
According to Gary Phipps, the stakeholders you have to engage vary depending on your industry, but in most cases, “the security officer usually has to make the decision as to what they’re going to do with whatever data they get from the third party.” The importance of executive buy-in can’t be overstated. As Mr. Phipps continues to explain, “The business can veto what the security officer offers as an opinion.”
However, once you have the right stakeholders on board, and your system is on its feet, it’s important to take an objective look at the data you get from each vendor. This is crucial because the ways in which companies report their security measures may be less than 100% forthright. Gideon Rasmussen highlights the problem this way: “The way auditors scope their assessment—they rely on the services report, which is written by the client.”
Mr. Rasmussen provides the following example: “ If I post a web app that you put sensitive data into and I don’t have a web app firewall, all I have to do is not indicate that on the service report, and it won’t show up on the profile for my company.”
This is why it’s so important to ask specific questions of each vendor as part of your TPCRM implementation process. This includes requesting artifacts that prove the veracity of their responses.
Pillar 3: Governance
Governance of your TPCRM program involves putting it in the hands of someone with a vested interest in its success. An audience poll showed most respondents have tasked third-party cyber risk programs to the risk management or security teams. A smaller percentage designates ownership to the IT team.
For those in the early stages of launching a TPCRM program, Mr.Rasmussen offered this advice, ”It begins with drumming up enthusiasm through a very simple presentation. It may be best to use only a single slide during a presentation that outlines the most compelling reasons why your organization needs a TPCRM program,” he said.
Then, the governance system needs to include controls that allow for at least some flexibility. This may involve two simple questions:
- Based on the information we have about the risk a third-party presents, can we use them?
- If we use them, do we need compensating controls to mitigate the risks they introduce to your organization?
Pillar 4: Sustainability
Ensuring the sustainability of your TPCRM program may depend on your forward-thinking strategy. As Shay Colson explains, “You have to look at the delta function of time—thinking about what you’re going to do next year or next quarter and what the mechanics are for triggering those assessments or next phases. The sustainability of your TPCRM program will also depend on how you deal with each vendor you work with, specifically, how you’re going to onboard vendors that come on with your organization.”
Similarly, Mr. Rasmussen says you need to plan out your chess moves well in advance. “I’m always thinking about program architecture. I try to think of a multi-year—three-year—plan.”
To ensure adequate funding, you need a little empathy, putting yourself in the shoes of decision-makers with limited funds. As Mr. Rasmussen puts it, you should “try to talk with the executive core about their thoughts on CAPEX versus OPEX. It’s important to both get as many resources as you can and also be sensitive to how your program will impact CAPEX and OPEX.”
Start or improve Your Scalable TPCRM Program Today
By focusing on the four pillars—strategy, process, governance, and sustainability—you can ensure your TPCRM program is not only effective but scalable. Be sure to get the right decision-makers behind your efforts by presenting compelling reasons why you need to build or improve your TPCRM program. Then plan ahead, making sure you have a well-defined system in place for onboarding each of your vendors.
By using objective data points gathered by a system that doesn’t depend solely on the input of third-party vendors, you can gain a more accurate understanding of the risks they introduce. Learn more about how this works by reaching out to CyberGRX today.
Meta: A scalable third-party cyber risk management (TPCRM) program is essential to minimize business disruption. Learn what it takes to build a scalable TPCRM program.
Related Articles
Join The GBI Impact Community
Sign up to make an impact and hear about our upcoming events
By registering anywhere on the site, you agree with our terms and privacy policy



